Microsoft is disabling Basic authentication in an effort to improve data security in Exchange Online. Starting October 1, 2022, Microsoft will begin turning off Exchange Online Basic authentication. (For more information, see the Microsoft article “Deprecation of Basic authentication in Exchange Online”).
As of September 2022, Microsoft has provided an update on guidance for the upcoming change to Basic authentication. The update can be found here, Basic Authentication Deprecation in Exchange Online. There is guidance around how to avoid disruption by requesting a one-time extension. These exception changes should give some breathing room to those that are not able to proceed by October 1st.
What Is Basic Authentication?
Basic authentication allows users and clients to send a simple username and password to Exchange Online for authentication. Typical Basic authentication can originate from several sources. For end users, you’ll see applications such as Apple Mail or other third-party email clients. From an administrative standpoint, we’re most concerned with applications or services that are configured to use Basic authentication and that will experience a business impact when Microsoft disables Basic authentication.
On October 1, Microsoft will begin requiring Modern authentication for accounts connecting to Exchange Online. Modern authentication also allows users and clients to send simple usernames and passwords, but it additionally allows other authentication steps such as multi-factor authentication (MFA) via Microsoft Authenticator. The removal of Basic authentication also removes password that do not include MFA.
Identifying Legacy Clients
Most Microsoft Azure tenants that have existed for a while will have some users or clients connecting to Exchange using Basic authentication. To minimize business or customer impact, organizations should determine by October 1 which of their clients or users are authenticating using Basic authentication.
You can leverage the Microsoft Azure Portal to determine which clients are using Basic authentication. Explore the Azure sign-In logs to identify legacy clients.
To find Basic authentication clients via the Azure Portal, follow these steps:
- Log on to https://portal.azure.com
- Go to Entra ID
- Under Monitoring, select “Sign-in logs”
- Select Columns and choose “Client credential type”
This will provide a list of sign-ins, including the client credential type. We’re primarily interested in the credential type “client assertion.” Filtering on client assertion will provide a list of all clients authenticating with Basic authentication.
Note that some organizations may be using a third-party identity provider (IDP) for authentication. In some cases when using a third-party IDP, the client credential type may show as “none” for some logins, because the authentication is occurring and being logged locally to the IDP.
In addition to filtering on client credential type, we can further drill into the results as follows:
- Select Columns and choose “Client app”
- Add a filter for “Client app”
- Select all of the “Legacy Authentication Clients,” as the following screenshot shows:
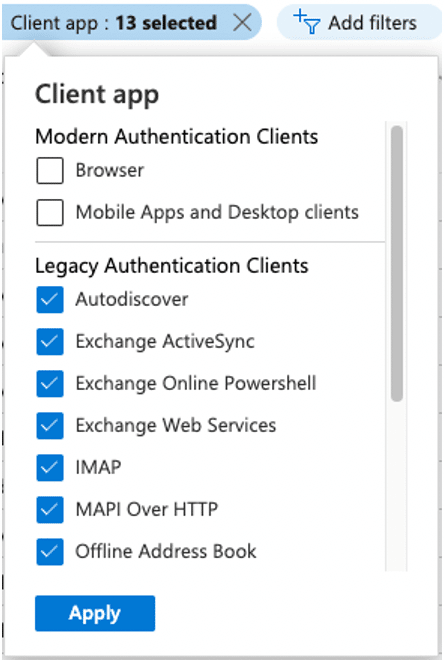
After filtering the list of sign-in logs via the Azure Portal, you can download the information as a CSV file and sort it to determine unique clients and applications. To download the results as a CSV file, click the Download button in the upper left-hand corner of the screen and select “Download CSV.”
Disabling Basic Authentication
Once you’ve determined which clients are using Basic authentication, you can use several methods to disable it: enforcing Conditional Access policies, disabling legacy authentication, or defining an Exchange Online authentication policy. Defining a Conditional Access policy will block access after authentication, whereas defining an Exchange Online authentication policy will block access before authentication.
Prior to disabling Basic authentication completely, you can create a Conditional Access policy in report-only mode. To create a Conditional Access policy to disable Basic authentication, follow these steps:
- Log on to https://portal.azure.com
- Go to Entra ID, Security, Conditional Access
- Select “New policy”
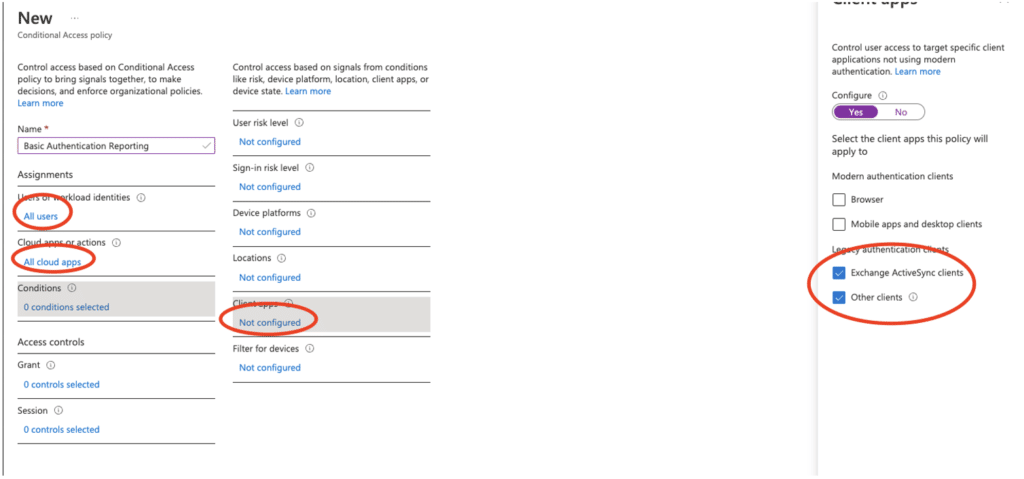
- Name the policy “Basic Authentication Reporting”
- Under “Users or workload identities,” select “All users” (or you could create a group of users to pilot with)
- Under “Cloud apps or actions,” select “All cloud apps”
- Under Conditions, select the legacy authentication clients, as the following screenshot shows, to configure client apps:
- Under Grant, select “Block access”
- Ensure that “Report-only” is selected under “Enable policy,” as the following screenshot shows:
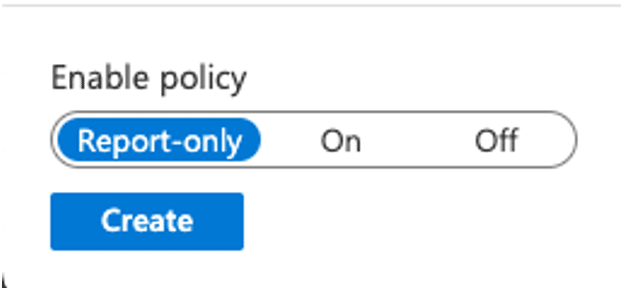
- Click Create
Once you’re sure the policy is running in report-only mode, you can then enable it.
As noted above, the Conditional Access policy only blocks app access after authentication. To completely block client access, deploy an Exchange Online authentication policy. The Microsoft article “Disable Basic authentication in Exchange Online” explains how to do so.
We recommend the Conditional Authentication policy as the best place to start. It gives you reporting functionality and is the quickest option to deploy.
Final Thoughts
The process of determining which clients are using Basic authentication and then disabling it can be time-consuming. If you need help with disabling Basic authentication before Microsoft deprecates it, Ravenswood Technology Group can help. Contact us today!