In the ever-evolving landscape of digital workspace solutions, Windows 365 emerges as a cloud-based PC deployment solution tailored for organizations seeking enhanced security and centralized control. With the advent of Windows 365, two key features come into play: Windows 365 Boot and Windows 365 Switch. In this blog, we’ll explore what these two services offer, as well as a few ways to improve the integration and experience. By leveraging Windows 365 Boot, IT administrators can designate physical devices as shared PCs, enabling users to sign directly into their Windows 365 cloud PCs. When converting these managed physical devices into shared PCs, users can no longer sign in locally on their devices. Microsoft has a guided setup that automatically creates the necessary configuration profiles to convert these target physical devices into shared PCs. A lightweight shell is deployed that replaces the regular Windows login screen with a login screen for the cloud PC. Once the user signs in with their Entra ID account, they are remoted onto their own cloud PC.
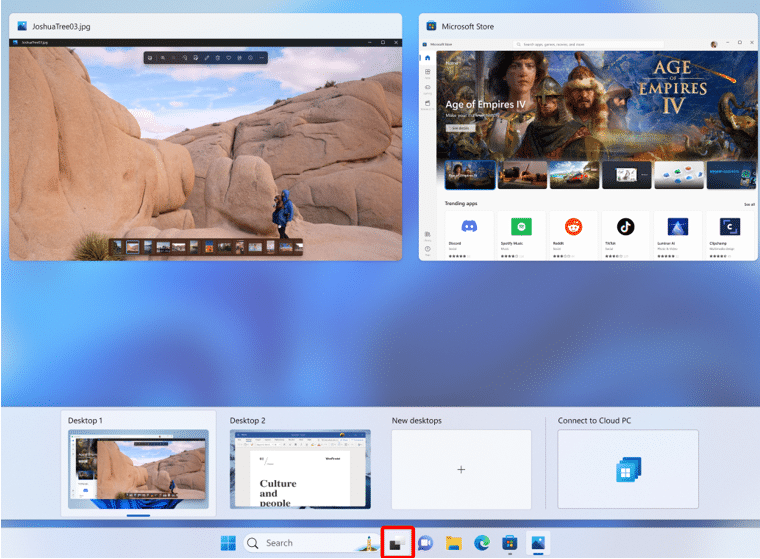
Windows 365 Switch, which is a separate feature from Windows 365 Boot, expands the access reach by allowing users to switch between their physical workstation and cloud PC. This feature works on Windows 11 Enterprise or Professional and is accessible through Task View, which has a similar user experience with Parallels Desktop for Mac. Selecting the “Connect to Cloud PC” option in Task View will switch the desktop to the cloud PC. The user can then move back and forth between the two desktops.
In today’s age of mobility and cloud-first focus, Windows 365 fills the gap between contractors using their personal devices and the organization provisioning managed devices for contractors’ time-limited usage. With Windows 365, contractors can securely access a cloud PC managed by the organization, thus ensuring an elevated level of protection and security.
Isolate Shared PC for Windows 365 Boot
When users connect to their cloud PCs from a shared PC, a secure Remote Desktop Protocol (RDP) connection is established, ensuring a safe and controlled environment for remote work. However, it is important to note that, by default, users accessing their cloud PCs from a shared device may have access to the shared PC’s resources and features.
For instance, users can execute CTRL+ALT+DEL and access Task Manager, allowing them to open applications such as File Explorer or a command prompt on the shared PC. Additionally, they may have access to features such as Change Password, Action Center, and shared PC notifications, which might not align with the desired level of isolation for sensitive work.
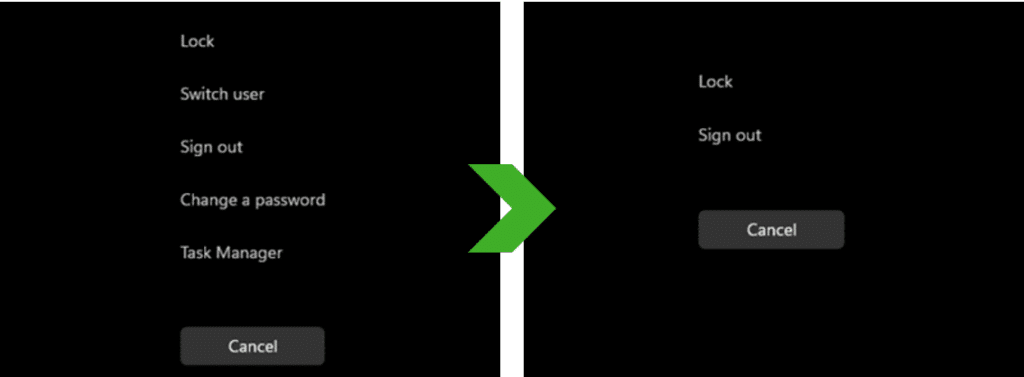
To address this concern, you can deploy a Microsoft Intune device configuration profile to the shared PC (or use Group Policy). This profile can also be applied to the cloud PC, ensuring consistency with the organization’s security policies. The configuration profile serves a critical role in removing or disabling these features on the shared PC, effectively creating an isolated environment while the user is logged on to their cloud PC.
By implementing these measures, you can enhance security and ensure that users accessing their cloud PCs from shared devices are operating within a controlled and isolated environment, minimizing the risk of unintended data exposure or unauthorized access to shared PC resources.
Enable Screen Capture Protection on a Cloud PC
In certain scenarios, a cloud PC may provide access to sensitive data where safeguarding data may be necessary. Notably, on Windows 10 and Windows 11 virtual machines, you can impose restrictions on screen capture, including screen recording.
When screen capture protection is configured, if an end user attempts to capture their screen, the entire cloud PC remote session will be concealed beneath a solid black overlay. This works with the session host, or cloud PC, instructing the remote desktop client to block screen capture on the remote session. Alternatively, you can configure screen capture protection on both the client and server, which also prevents services within the session host from screen capture.
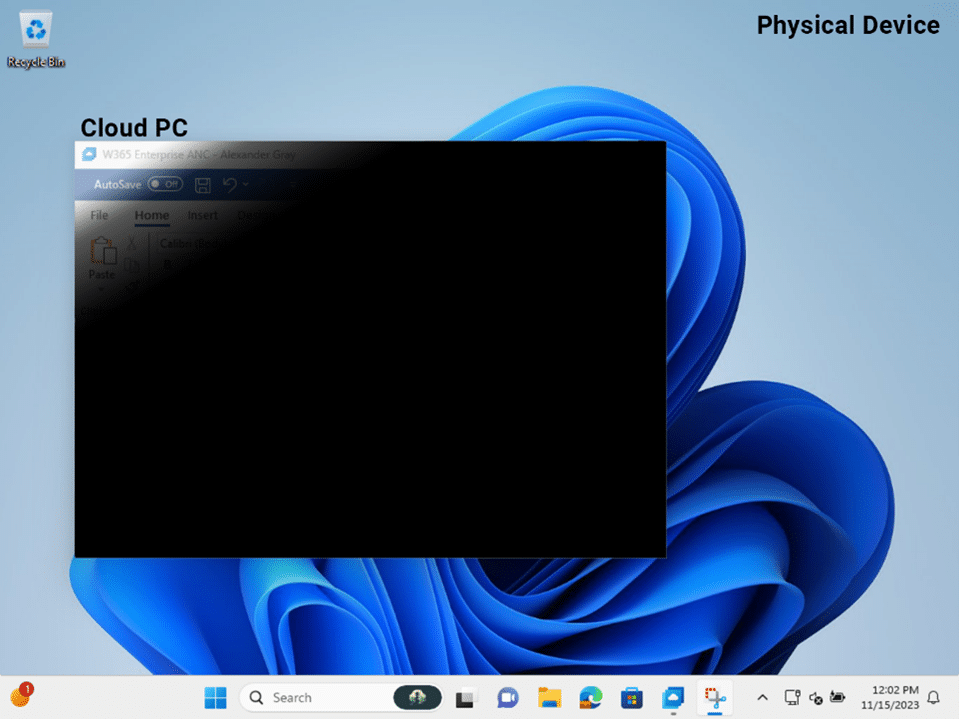
Although screen capture protection is highly effective in defending against screen shot or screen recording attempts, it is not bulletproof. For example, end users still retain the capability to share their screens through applications such as Microsoft Teams within the cloud PC. In addition, you cannot prevent users from taking a picture of the screen with their phone. You can mitigate these risks by applying a watermark to the cloud PC.
Client vs. Server
Breaking this down further, it is worth distinguishing between enabling screen capture protection for the client or both the client and server. In this context, the client represents the device from which the end user initiates the connection, whereas the server refers to the cloud PC to which they are connecting. Enabling protection solely for the client allows end users to screen-capture directly from the cloud PC but restricts them from capturing on the device from which they remote. However, when deemed necessary and when the security requirements align, enabling both client and server protection can provide an additional layer of security and further enhance data protection.
User and Device Structure
At a high level, the Windows 365 user and device structure follows a well-defined process. Initially, a group of users is assigned to a provisioning policy. This policy determines the number of cloud PCs automatically provisioned and specifies which users will receive access to them. Once this initial setup is in place, Windows 365 Switch can be employed. This simplifies the deployment process and ensures that users can swiftly transition to their cloud PCs with little administrative overhead.
However, when Windows 365 Boot is introduced, a guided setup is initiated, resulting in the creation of several essential Intune resources. These resources are customized with a prefix chosen by the administrator and are subsequently assigned to a group containing the devices intended for Windows 365 Boot, specifically shared PCs.
Device Filters for Windows 365
Implementing device filters is crucial when both Windows 365 Switch and Windows 365 Boot are concurrently in use. Filters provide granular control when assigning applications, policies, and profiles to devices and users. Device filters are created by setting rules that match certain criteria, such as a user’s department attribute or a computer’s manufacturer. When assigning a profile to a group, you can further refine filtering by applying the device filter to the assignment.
For shared PCs, filter criteria may vary depending on the specific environment. A straightforward approach to creating a filter for shared PCs involves using the device name, following a naming convention such as:
(device.deviceName -startsWith "WT-W365-SPC")
Assuming this naming convention is in place for shared PCs, you can assign users to a resource and apply an “include” filter, ensuring precise control.
When dealing with cloud PCs, a distinct advantage lies in the model attribute. All cloud PC models begin with “Cloud PC,” making it easy for administrators to create filters since the model is stored on the device’s object in Entra ID. Additionally, the model includes license identifiers and hardware configurations, providing flexibility in defining filter criteria. You can employ filters such as:
(device.model -startsWith "Cloud PC") (device.model -startsWith "Cloud PC") and (device.model -contains "Enterprise") (device.model -contains "2vCPU/8GB")
In environments where the same user account is used for both the primary workstation and a cloud PC, filters become indispensable. By implementing filters strategically, you can extend the same principles applied to shared PC filtering. When taking advantage of both Windows 365 Boot and Switch, a couple of ways to employ device filters is to use the filters to negate cloud PCs from assignment or targeting cloud PCs for specific departments.
Ease of Management Meets Ease of Use
Windows 365 presents a compelling solution for organizations looking to enhance security, centralize control, and streamline access to cloud-based PCs. With features like Windows 365 Boot and Switch, you can effectively manage not only cloud PCs but also shared PCs. With the ever-changing security landscape, it is vital to have the appropriate toolset to protect the user, device, and organizational data. By integrating with Intune, Windows 365 sets itself apart as a viable alternative to Azure Virtual Desktop deployments.
Need help navigating Windows 365 Boot and Switch? Contact the experts at Ravenswood Technology Group today.










