Do you know how to protect organizational data on mobile devices without affecting personal data? Are you aware of the policies required to implement a strong foundation for protecting your organizational data on users’ mobile devices?
Intune app protection policies help organizations protect their data. You can implement this technology with enrollment, known as Mobile Device Management (MDM), or without enrollment, sometimes referred to as Mobile Application Management without enrollment (MAM-WE) or simply MAM.
The true power of Intune MAM policies is the ability to force policy on organizational data without needing to enroll any devices. This is a big reason many organizations are currently implementing these policies for not only personal (BYOD) mobile devices but also corporate-owned mobile devices—and choosing to completely forego MDM solutions.
Intune MAM Components
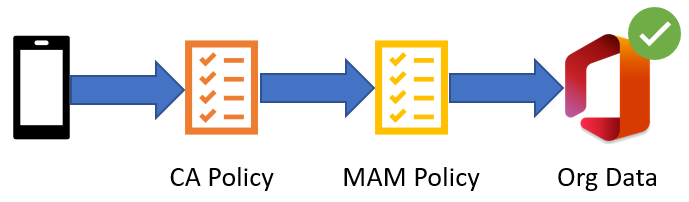
Two components make Intune MAM work: an Entra (formerly Azure Active Directory) Conditional Access (CA) policy and Intune MAM policies. CA policies are evaluated first. If a CA policy has a requirement to evaluate an Intune MAM policy, the client will evaluate the Intune MAM policy after the CA policy has been evaluated. The following figure illustrates this process.
CA policies are configured in the Entra ID portal on the Conditional Access blade. The Conditional Access Administrator role or equivalent permissions that exist in any other delegated role are required to create CA policies.
Make sure you have a test user in an Entra group and a test iOS and/or Android device to ensure the policies are configured correctly. You’ll likely come across individuals who require exemption from these policies, so you’ll need to create exclusion groups to accommodate these scenarios. Use the report-only mode and always review the sign-in logs for the new CA policies before enabling any policies. Implement these policies with your first pilot group, receive feedback, and iterate. Your first pilot group should be other IT members and business users who like to try new things and aren’t afraid of being the “canary” in your “coal mine.”
Implementing the Policies
To properly protect all organizational data on mobile devices, you’ll need three CA policies and two Intune MAM policies. Two of the CA policies are for blocking legacy protocols that users could otherwise use to bypass your Intune MAM policies and leave organizational data exposed. One of the CA policies is used to block basic authentication. Basic authentication relies on the use of simple username and password pairs that have no concept of multi-factor authentication, which is critical for corporate security. Another CA policy is for blocking Exchange ActiveSync. ActiveSync has been widely used by organizations and has become susceptible to attack in recent years, which is why Microsoft developed a new proprietary mechanism for its Outlook client. The third CA policy simply directs users to the Intune MAM policies.
You’ll need separate Intune MAM policies for Android and iOS. There are no large differences between the settings that are available; however, Android has a couple of more granular options for screen shots and soft keyboards. Don’t be shy about which apps you’re targeting in each of the Intune MAM policies. Just because you don’t own a license for a particular service such as Dynamics, or you don’t think your users are using a specific service that you already have, doesn’t mean you shouldn’t protect your data in those apps. You can always deselect the apps in the future if your organization wants to accept the risk.
Be aware that many third-party apps such as Zoom simply use the Intune SDK to wrap their app and make it compatible with Intune MAM policies. Unfortunately, this has created confusion for end users and admins alike. This approach means users must install an entirely separate app (e.g., Zoom for Intune) to continue working with organizational data. Some third-party apps, such as Adobe Acrobat, natively integrate Intune MAM technology but require users to enable the MAM technology within the app’s settings to continue accessing organizational data.
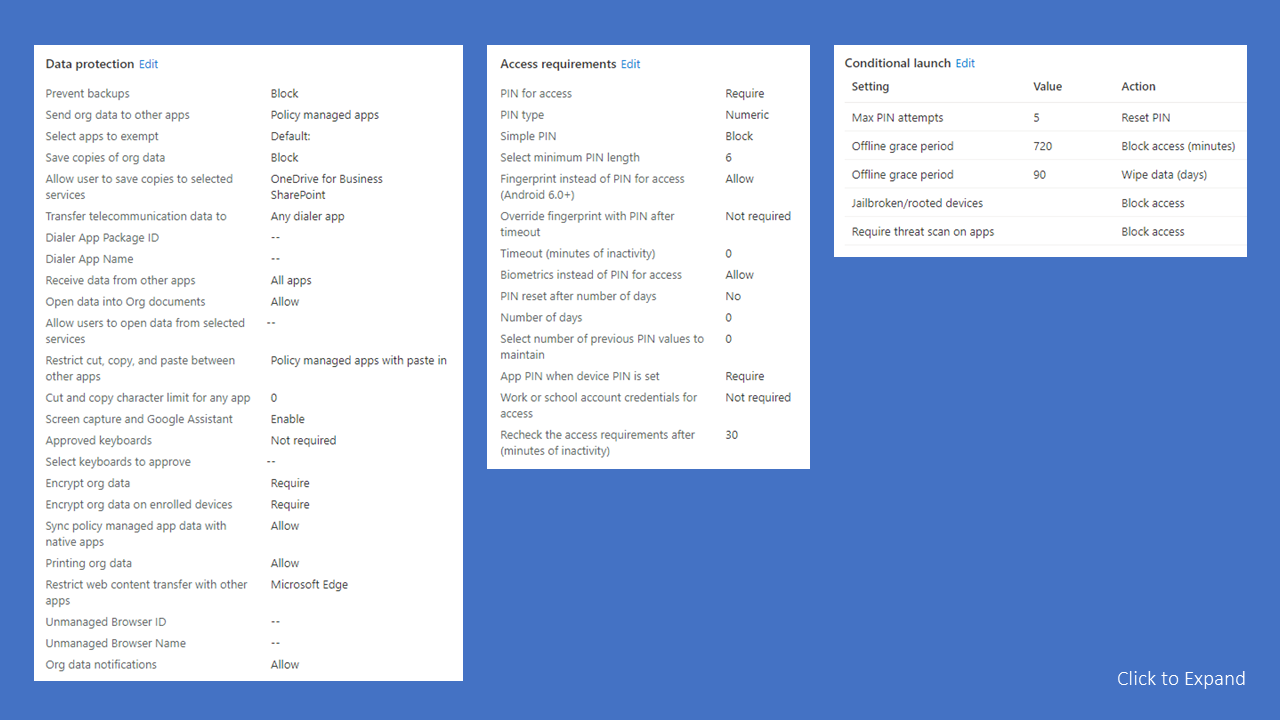
Most of Microsoft’s default settings are acceptable, but you may want to force your users to store organizational data on OneDrive and SharePoint. Excluding local storage prevents users from backing up organizational data to iCloud or Google Drive. You may also want to enforce PIN complexity and allow users to use biometrics. The following screen shots provide examples of these types of restrictions.
Implement, Test, Deploy
To protect your organization’s data on users’ mobile devices, you need to implement CA policies and then Intune MAM policies. Next, you should apply the policies to pilot users who have test devices. Once you’ve completed a proper pilot test, you can apply the policies to everyone in the organization.
If you need assistance with deploying Intune MAM in your organization, contact Ravenswood Technology. We’re here to help!