Windows Local Administrator Password Solution (LAPS), now integrated into the OS, is the replacement for Microsoft LAPS, which was a separate installation. Windows LAPS is a native, built-in solution with increased functionality and security features. It also provides an emulation mode to help you migrate from legacy Microsoft LAPS. Now is the time to migrate to Windows LAPS and harden your local accounts’ security.

For the purposes of this blog post, we will refer to the original version of LAPS as legacy LAPS, and we will refer to passwords as secrets. We will also assume that you have already deployed legacy LAPS in your environment and are familiar with how it works.
Windows LAPS Overview
Partner with Microsoft experts you can trust
If it’s time to take that first step toward leveling up your organization’s security, get in touch with Ravenswood to start the conversation.
Windows Local Administrator Password Solution (LAPS) is a simple yet powerful tool provided by Microsoft that addresses a significant security risk in organizations—managing the local administrator passwords of Windows computers. Before LAPS, IT administrators often set the same local administrator password across all machines, or they managed multiple passwords manually, both of which posed substantial security risks. LAPS automates the process of generating and storing unique, complex passwords for the local administrator account on each Windows PC. These passwords are stored securely in Active Directory (AD) or Entra ID and can be accessed only by authorized users.
One of the main benefits of Windows LAPS is its enhancement of security by ensuring that each computer has a unique administrator password. This minimizes the potential damage from pass-the-hash and brute force attacks. LAPS is also highly beneficial for compliance, as it helps organizations meet standards that require unique credentials for administrative accounts. Moreover, the tool includes automatic password expiration, further securing systems by regularly updating credentials without requiring manual intervention.
Improvements in the newer versions of Windows LAPS over its predecessors include better integration with AD, password storage in Entra ID, streamlined management through a graphical user interface (GUI), and enhanced security features such as support for longer and more complex passwords. Additionally, the updated LAPS provides more robust auditing capabilities, allowing organizations to track and monitor password changes and access more effectively. These enhancements make LAPS an indispensable tool for modern Windows environments, promoting more secure and manageable administration of machine-level privileges.
What Is Different?
The enhancements that Windows LAPS provides over legacy LAPS include the following:
- Time-bound usage of managed secrets after authentication occurs
- Managed secrets encrypted at rest
- Management of Directory Services Restore Mode (DSRM) secrets
- No additional installation; built in to modern Windows versions
- Secret history review
- Option to manage policies using a mobile device management (MDM) solution such as Intune
- Option to store managed secrets in Microsoft Entra ID (formerly known as Azure Active Directory—AD)
Client operating system requirements are:
- Windows 10 or later (April 2023 monthly update)
- Windows Server 2019 or later (April 2023 monthly update)
No new requirements exist for domain controllers if you are initially performing a like-for-like migration. As you start to think about using encryption to protect managed secrets, implementing secret history, and managing DSRM secrets, you will need to have the domain functional level set to at least Windows Server 2016 in the domains where you have Windows LAPS policies deployed.
The Windows LAPS client uses its own set of AD attributes, separate from attributes used by legacy LAPS, so a separate AD schema update is required. Due to these different attributes, you must also grant managed computers SELF permissions to write to the new LAPS attributes.
A separate PowerShell module called LAPS performs Windows LAPS-related activities, whereas legacy LAPS used AdmPwd.PS. The cmdlets in the LAPS PowerShell module have a noun prefix of LapsAD.
Computers that are no longer in emulation mode will require the Microsoft Management Console Active Directory Users and Computers snap-in or the Active Directory Administrative Center (ADAC)—or the LAPS cmdlets—to manage the LAPS-related secret information. Figure 1 shows an example. You will no longer use the legacy LAPS UI or related PowerShell cmdlets.
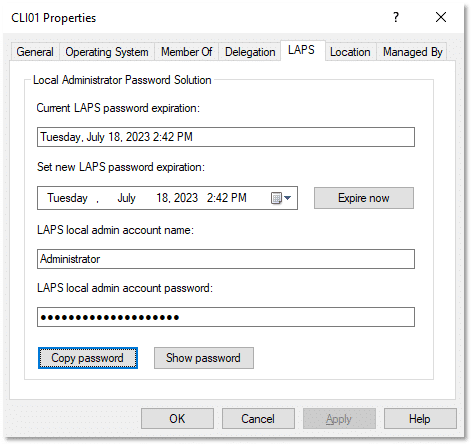
Figure 1
To retrieve Windows LAPS secrets using PowerShell, use Get-LapsADPassword, which is great for bulk operations. If the secret is encrypted and you have permission to decrypt it, you will need to include the -AsPlainText parameter with the cmdlet to display the secret, as the following code output shows.
PS C:\ > Get-LapsADPassword -Identity cli01
ComputerName : CLI01
DistinguishedName : CN=CLI01,CN=Computers,DC=cohovines,DC=com
Account : Administrator
Password : System.Security.SecureString
PasswordUpdateTime : 6/18/2023 2:42:38 PM
ExpirationTimestamp : 7/18/2023 2:42:38 PM
Source : EncryptedPassword
DecryptionStatus : Success
AuthorizedDecryptor : Lab\LAPSAdmins
PS C:\ > Get-LapsADPassword -Identity cli01 -AsPlainText
ComputerName : CLI01
DistinguishedName : CN=CLI01,CN=Computers,DC=cohovines,DC=com
Account : Administrator
Password : vIP57{0k6U#g2AX7onq2
PasswordUpdateTime : 6/18/2023 2:42:38 PM
ExpirationTimestamp : 7/18/2023 2:42:38 PM
Source : EncryptedPassword
DecryptionStatus : Success
AuthorizedDecryptor : Lab\LAPSAdmins Events raised for LAPS management are now stored in the Microsoft-Windows-LAPS/Operational log. Computers in emulation mode and native Windows LAPS mode will record events here. A device in emulation mode will raise event 10023, as the following output shows.
The current LAPS policy is configured as follows: Policy source: LegacyLaps Backup directory: Active Directory Local administrator account name: Password age in days: 30 Password complexity: 4 Password length: 14 Password expiration protection enabled: 0 See https://go.microsoft.com/fwlink/?linkid=2220550 for more information.
Computers in native Windows LAPS mode will have a policy source of GPO instead of LegacyLaps and raise event 10033.
The machine is configured with legacy LAPS policy settings but a legacy LAPS product appears to be installed. The configured account's password will not be managed by Windows until the legacy product is uninstalled. Alternatively you may consider configuring the newer LAPS policy settings.
Windows LAPS policy settings are stored in new administrative template files, separate from legacy LAPS policy settings, even though some of the settings behave the same.
Begin the Migration
In a heterogeneous environment where you have systems that are not yet running on supported versions of Windows 10/11 or newer, or Windows Server 2019 or newer, you need to maintain the legacy LAPS policy settings.
- Since Windows LAPS isn’t something that you install, you can’t create a local administrator account as part of the installation because you aren’t installing a software package. Legacy LAPS supported this, so if you were using the legacy LAPS .msi file to create a separate administrative account, you will need to find a different solution prior to migration.
- For the versions of Windows that support Windows LAPS, you can leverage emulation mode. This allows you to continue using the legacy LAPS policy settings before transitioning to the Windows LAPS settings. Emulation mode is an automatic behavior and is not explicitly configured.
- The LAPS ADMX and ADML files can be found on supported versions of Windows at
%windir%\PolicyDefinitions. Copy the LAPS.admx and LAPS.adml files to your policy store. - Extend the AD schema to support Windows LAPS. To do so, run the following cmdlet with an account in the Schema Admins group:
Update-LapsADSchema
After running this cmdlet, the following new attributes are added to the Computer object class:
- ms-LAPS-Password
- ms-LAPS-PasswordExpirationTime
- ms-LAPS-EncryptedPassword
- ms-LAPS-EncryptedPasswordHistory
- ms-LAPS-EncryptedDSRMPassword
- ms-LAPS-EncryptedDSRMPasswordHistory
- ms-LAPS-Encrypted-Password-Attributes
- Grant the managed device permission to update its secret. To do so, run the following cmdlet:
Set-LapsADComputerSelfPermission -Identity 'dc=cohovines,dc=com'
This example is targeting the domain root, but you can target a specific organizational unit (OU) instead by providing the appropriate distinguishedName value for the Identity parameter.
After running this cmdlet, computers will be able to update the following attributes of their computer account:
- msLAPS-Password
- msLAPS-PasswordExpirationTime
- ms-LAPS-Encrypted-Password-Attributes
- Apply Windows LAPS policy settings for clients that support Windows LAPS to stop using emulation mode. These settings can be found in a Group Policy Object at the following location, as Figure 2 shows:
Computer Configuration > Administrative Templates > System > LAPS
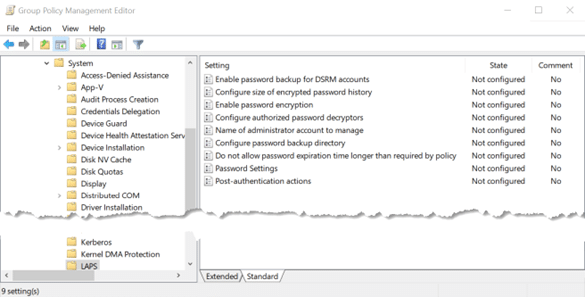
Figure 2
You may choose to keep the existing legacy LAPS settings in place if unsupported Windows devices are in the same OUs as supported Windows devices. When legacy LAPS settings and Windows LAPS settings are applied to a supported client, the client will only apply the setting that is defined by Windows LAPS. When a client is no longer applying any legacy LAPS settings, it is no longer in emulation mode.
- Remove the legacy LAPS software from computers that are no longer in emulation mode. The following command will uninstall the legacy LAPS client:
MsiExec.exe /x {97E2CA7B-B657-4FF7-A6DB-30ECC73E1E28} - Clear the ms-Mcs-AdmPwd and ms-Mcs-AdmPwdExpirationTime legacy attributes on computer objects that are no longer in emulation mode. You can use Set-ADComputer as shown in the example below.
Set-ADComputer -Identity cli01 -Clear ms-Mcs-AdmPwd,ms-Mcs-AdmPwdExpirationTime
- If you were able to remove all legacy LAPS policy settings in the domain, remove the legacy LAPS administrative template files in your policy store, which are named AdmPwd.admx and AdmPwd.adml.
Summary
There are many reasons to migrate to Windows LAPS. Following the steps outlined here should help you quickly complete your migration. If you are interested in migrating to Windows LAPS to store your secrets in AD or Microsoft Entra ID and would like help, reach out to the experts at Ravenswood Technology Group. Contact us today!











