When you hear the phrase “art of deception,” you might think of street magicians dazzling crowds of onlookers with their sleight of hand tricks and illusions. For me, it brings to mind fishing.

The art of deception is key to turning fishing into catching. Using lures that mimic natural prey and lifelike movements to entice fish to bite are essential techniques. Understanding the fish’s habitat and patterns and strategically placing lures where bass hide is crucial. If it looks fake or out of place, the fish won’t bite. Patience and practice make the art of deception vital for a successful fisherman.
Just as anglers use clever tactics to lure fish, cyber security teams can now harness the power of deception technology built into Microsoft Defender XDR to catch cyber intruders. By deploying lures and decoys that look and feel authentic, these teams can entice cyber intruders to take the bait, triggering alerts that enable the cyber defenders to swiftly identify and expel the threat. This proactive approach of luring predators to take the bait helps bolster an organization’s data security and prevent the compromise of highly privileged accounts.
What is deception technology?
Partner with Microsoft experts you can trust
If it’s time to take that first step toward leveling up your organization’s security, get in touch with Ravenswood to start the conversation.
Deception technology is a proactive approach to endpoint security that employs realistic lures and decoys distributed throughout the corporate network to attract and mislead intruders, thereby alerting security teams to their presence. These lures include fake data, host systems, and accounts that mimic the natural “prey” of an attacker.
To help security teams find and expel unwanted intruders in the corporate network, Microsoft introduced built in deception technology in its Microsoft Defender XDR offering.
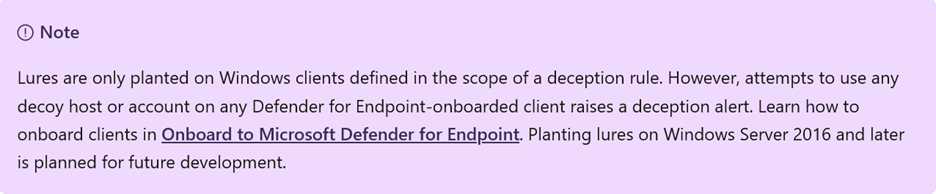
Microsoft Defender XDR Deception technology is currently in public preview and supports Windows clients only. Support for Windows Server 2016 and later will be included in a future release. The deception capability overview page at Microsoft Learn has this to say about its public preview offering:
Microsoft Defender XDR Deception utilizes rules that you can create to deploy lures and decoys within the corporate network, embedding fake data or fake credentials on devices strategically placed by corporate defenders. For a lure or decoy to be effective, it must convincingly resemble real bait, which is why Microsoft Defender XDR leverages machine learning to create highly realistic decoys. When attackers take the bait, alerts are sent to security teams in real time for a swift response. You can learn more about Microsoft Defender XDR’s deception technology on the Microsoft Learn website: Manage the deception capability in Microsoft Defender XDR – Microsoft Defender XDR | Microsoft Learn.
Benefits of deception technology
Deception technology is foremost a proactive defense mechanism that offers four key benefits when integrated into a defense-in-depth strategy. These benefits include valuable insight like enhanced threat detection, diversion of attackers, delaying the attacker and buying critical time for response, and ultimately dislodging the attacker from the network.
- Detect – Reveals the presence of an attacker and their tactics.
- Divert – Keeps the attacker busy causing them to spend time and resources on decoy assets.
- Delay – Allows time for defenders to respond to a cyber-attack by confusing and misleading attackers before any real damage can occur.
- Dislodge – By detecting their presence, diverting their attention to decoy systems, and delaying the human-operated attacker, defenders may remediate the vulnerabilities that allowed access, evict the attacker from the network, and seal the gaps that permitted entry.
How to deploy Microsoft Defender XDR deception technology
Deploying Microsoft Defender XDR deception technology is straightforward and designed for ease of deployment. Microsoft customers with Microsoft 365 E5, Microsoft Security E5, or Microsoft Defender for Endpoint Plan 2 may start leveraging deception technology right away.
Additional Requirements:
- Defender for Endpoint should be the primary EDR solution.
- Automated investigation and response capabilities in Defender for Endpoint must be configured.
- Devices must be joined or hybrid joined to Microsoft Entra.
- PowerShell must be enabled on the devices (in non-restricted/non-constrained mode).
- The deception feature is available for clients operating on Windows 10 RS5 and later in preview.
- Assigned one of the roles: Global administrator, Security administrator, Manage portal system settings.
Deploying Defender for Endpoint is beyond to scope of this blog, but you can find more information on Microsoft Learn at: Onboard to Microsoft Defender for Endpoint – Microsoft Defender for Endpoint | Microsoft Learn. Once all of the prerequisites have been met, follow these steps to deploy Microsoft Defender XDR Deception:
- Open a browser and navigate to https://security.microsoft.com.
- Log in using one of the roles listed in the requirements section.
- Scroll to the bottom of the left pane and select Settings.
- Within the Settings pane, select Endpoints.
Select Advanced features and scroll to the bottom of the right pane to turn on Deception, then save your preferences. If you do not see Deception in your tenant, scroll to the bottom of the page and turn on “Preview features”, then refresh the page. It will take a few minutes for Deception to show up.
Create detection rules
A deception rule specifies the parameters of a deception campaign, detailing which devices are included in the scope and outlining the specific decoys and lures to be deployed. These rules are crucial for effectively simulating realistic scenarios that can mislead attackers and trigger alerts for the cybersecurity team. Microsoft already provides a default rule that can be deployed or used as an example of how a deception rule is created. I’ll duplicate the default rule below to create a new one, just to demonstrate a simple example.
- Within the Settings > Endpoint pane, click Deception rules and you are taken to the list of existing deception rules and can see the Default Rule provided by Microsoft.
- To create a new rule, click the + Deception rule.
- Give the rule a name and description and select Basic and Advanced lure types and click Next.
- Define the rule scope to choose all Windows client devices or you can select device with specific tags. (For this first rule, we will select all Windows devices which places a lure on all devices.)
- In the manage decoy accounts and hosts, you may choose to use the auto-generated lures or create your own then click Next. We will use the auto-generated accounts for now.
- In the Lures window, you may select to use auto generated lures or upload your own. Select Use Autogenerated and click next.
- Review the rule and then click save. (Note: It will take several hours to deploy the lures and start generating alerts.)
The point of this exercise was to demonstrate how easy it is to create a rule, if all the prerequisites are in place. Any attempts to access the lure will result in an alert with the tag “Deception” indicating one of your deception rules was triggered and a threat actor is trying to gain access.
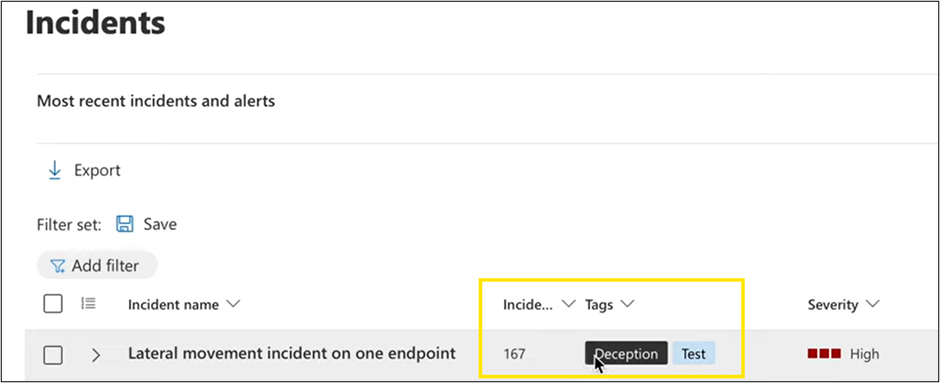
You’ve just created your first rule. Keep in mind that one limitation to the public preview is a maximum of 10 deception rules. Each deception rule you create represents a different campaign. Campaigns are comprised of the specific decoys, lures, scopes, and alerts you are targeting. Multiple campaigns may be used to target different cyber threats, network segments, and timeframes. If you decide to upload your own custom lures, you can use any file type except .DLL or .EXE files.
Watch for my next blog post where I’ll delve a bit deeper into designing a deployment approach and creating custom rules and lures that can be deployed to specific hosts within a network.
Summary
Deception technology is a powerful tool in the cybersecurity arsenal, providing proactive defense mechanisms that enhance threat detection, divert attackers, delay attackers and buy critical response time, and allow security defenders to dislodge attackers from the network. By integrating Microsoft Defender XDR’s deception technology, organizations have another threat intelligence tool to add to their defense-in-depth strategy.
At Ravenswood Technology Group, we specialize in helping organizations design, implement, and manage their Active Directory and Microsoft Entra environments. If you need help getting started, review some of our other blogs such as
- 2024 Guide to Privileged Access Workstations: Enhance Security
- Active Directory Design Overview | AD Security
- Insider Risk Management | Advanced Data Loss Prevention
We can also work with your team to provide an assessment using our Active Directory Health Check – Ravenswood Technology Group.
Get in touch with Ravenswood Technology Group today to learn how we can help you achieve a well-designed, secure, and efficient Active Directory and Microsoft Entra environment.










