All organizations use privileged accounts to manage their environments. In many cases, administration is performed from productivity workstations, which are vulnerable to a substantial number of attack vectors.

A key component in securing privileged access is performing privileged administration from secure workstations, also known as privileged access workstations (PAWs). PAWs are purpose-built, hardened computers that are configured with a reduced attack surface. Minimizing the ways that an adversary can compromise the workstations used for administration is crucial in preventing bad actors from gaining elevated access.
Who should use PAWs? Ideally, all administrators who have access to systems or data that, if compromised, could cause serious damage to an organization or its reputation should use a PAW. This includes but is not limited to administrators with elevated access to identity systems such as Active Directory and Microsoft Entra ID, as well as administrators with privileged access to cloud services and hypervisors that host business-critical systems and data.
Intermediaries and Interfaces
Partner with Microsoft experts you can trust
If it’s time to take that first step toward leveling up your organization’s security, get in touch with Ravenswood to start the conversation.
Intermediaries are systems that are sometimes used to gain access to the environment’s interfaces. Examples of intermediaries include VPNs, third-party privileged identity management (PIM)/privileged access management (PAM), jump servers, Azure Bastion, Microsoft Entra PIM, and Application Proxy solutions. When intermediaries are used for privileged administration, they are privileged intermediaries.
Interfaces include web portals, desktop consoles, or scripting interfaces. Examples of web portals include the Azure portal, Intune portal, AWS Management Console, and Google Cloud console. Some interfaces can be accessed directly, and others are accessed through an intermediary. The Microsoft Management Console, vendor app consoles, and scripting interfaces such as PowerShell or SSH are examples of desktop console interfaces. Interfaces that are used for administration of identity systems and business-critical systems are privileged interfaces.
PAWs are just one component of a complete privileged access strategy. Other essential components are secured privileged accounts, privileged intermediaries, and privileged interfaces. To adhere to the clean source principle, you must use PAWs to manage privileged intermediaries and interfaces. We’ll discuss the clean source principle in a later section.
Reduced Attack Vectors
PAWs are configured to have a minimal number of attack vectors. This increases the investment an adversary must make to compromise the administrative workstation. The most common attack vectors that plague productivity workstations are email and unconstrained web browsing.
PAW users are prevented from using email; the Exchange Online (Plan 2) service is disabled in their Microsoft 365 license so that it is no longer available. This eliminates the possibility of an email phishing attack on the account used to log on to PAWs.
Productivity workstations are typically permitted to browse to most websites that are not in clear violation of company policies. Unfortunately, this does not always protect users from browsing to malicious websites. For this reason, only approved websites are accessible from PAWs.
PAW users are also configured as standard users and do not have local administrator rights, nor are they permitted to temporarily elevate. This helps prevent undesired software installation and configuration changes being made to the PAW. All software installed on PAWs is delivered using a trusted managed system (e.g., Microsoft Intune).
Differences Between a Productivity Workstation and a PAW
Outside of email and web browsing restrictions, you may be questioning what the differences really are between a productivity workstation and a PAW. In your organization, you’ve likely taken numerous steps to secure end-user workstations. At a minimum, storage is encrypted using BitLocker, agents are deployed for an XDR/EDR solution such as Defender for Endpoint or CrowdStrike, and devices are configured with baseline security settings from Microsoft or the Center for Internet Security (CIS).
So why not just deploy a secondary workstation for administrators and have them log on with their privileged account? Although somewhat helpful, the security dependencies of the PAWs themselves also need to be addressed.
Many of the same mechanisms used to secure productivity workstations are also present with PAWs; however, PAWs include additional security configurations. This added hardening is not typical of productivity workstations due to the balance that must be attained between functionality and security. Since PAWs are dedicated devices used exclusively for privileged administration, the balance is shifted further toward security, while still allowing for privileged administration to be unencumbered. Table 1 shows the main configuration differences between productivity workstations and PAWs.
Table 1: Productivity Workstations vs. PAWs
Productivity Workstations | PAWs | |
|---|---|---|
Secure boot | X | X |
Credential Guard | X | X |
TPM 2.0 | X | X |
BitLocker encryption | X | X |
Windows Hello for Business | X | X |
Intune security baselines | X | X |
Local admin rights and temporary elevation removed | Some | X |
URL restrictions | Some | X |
AppLocker (application execution control) | X | |
Applications only installed by Intune | X | |
Windows Defender Application Control (WDAC) | X | |
Windows Firewall outbound traffic blocked by default | X |
Clean Source Principle
The clean source principle dictates that any user, device, or system that can exert control on a downstream user, device, or system becomes a security dependency. These security dependencies must be accounted for when designing privileged access strategies.
The tiered access model states that the control paths of lower-tiered administrators (e.g., Tier 1 and Tier 2) should be blocked from controlling higher-tiered resources (e.g., Tier 0). Implementing a tiered access model helps prevent Tier 1 administrators from elevating their privileges and controlling higher-tiered (Tier 0) resources and Tier 2 administrators from exerting control on either Tier 0 or Tier 1 resources.
If the security dependencies are not addressed, lower-tiered administrators or an attacker who has compromised their credentials could take control of a higher-tiered resource. PAWs should be used to administer any privileged downstream users, devices, and systems.
The clean source principle is illustrated in Figure 1.
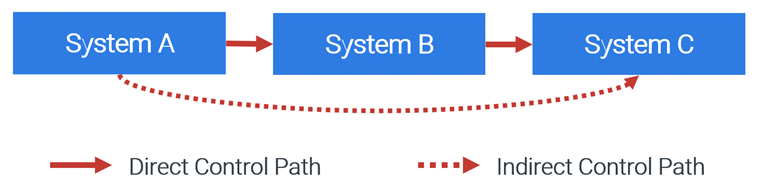
Figure 1. Clean source principle
Example: Compromise of a Tier 2 Resource Leads to Compromise of a Tier 0 Asset
Numerous attacks are possible if the clean source principle is not followed. The following example shows how a lower-tiered (Tier 2) administrator’s workstation could be used to gain elevated access to a Tier 0 administrator’s workstation and then grant privileged access in Active Directory. This example scenario is depicted in Figure 2.
Components
- System A: Tier 2 administrator workstation
- System B: Tier 0 administrator workstation
- System C: Tier 0 asset (Active Directory domain controller)
Scenario
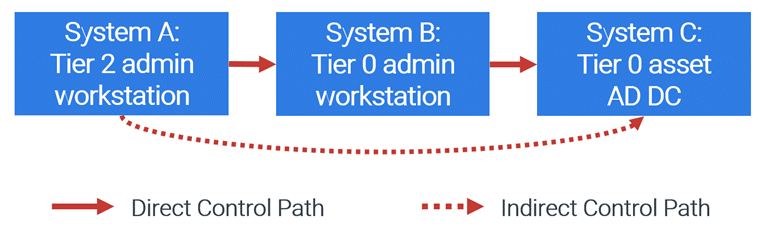
Figure 2. Using a Tier 2 admin workstation to gain Tier 0 access
- The workstation team (Tier 2 administrators) has management capabilities of System B. They control the Intune configuration profiles and distribution of software on System B, which is used by a Tier 0 administrator.
- An attacker compromises System A by performing a phishing attack on a Tier 2 administrator.
- The attacker uses System A to push legitimate remote support software to System B, giving them remote control.
- The attacker runs PowerShell commands from System B to create new accounts in Active Directory and add them to sensitive groups. This can allow the attacker to make malicious changes in Active Directory or gain access to critical systems and data.
The PAW Value Proposition
The entire build, configuration, and management process for PAWs follows the clean source principle. This is accomplished by ensuring lower-tiered administrators and systems are not allowed to exert control over PAWs or the systems used to build and manage them.
Risks that typically afflict productivity workstations are mitigated on PAWs by implementing security configurations such as:
- PAW users are disallowed from being email enabled, thus thwarting phishing attacks.
- Restricted internet access prevents accidental malware downloads.
- PAW users are configured to be standard users rather than administrators on their PAWs. They are also not allowed to elevate to administrator, even temporarily. This prevents PAW users from installing unauthorized software and making system configuration changes.
- WDAC is used to control which drivers and applications are permitted to run. Verification of codesigning certificates used for signing driver and application binaries is performed and prevents untrusted drivers and application binaries from running.
- AppLocker is used to further restrict the applications allowed to run on a PAW. This helps prevent malicious or unapproved software from being executed.
- Windows Firewall outbound traffic is blocked by default, which helps prevent data exfiltration and malware communications.
These security controls (and many more) collectively harden PAWs and make them a much less attractive target for adversaries. This protection prevents privileged credentials and sessions from being attacked at the point they are first used (the PAW) and mitigates a myriad of risks.
Summary
Your privileged access strategy should include PAWs. PAWs are purpose-built, hardened workstations that have additional security configurations and reduced attack surfaces to help prevent adversaries from gaining privileged access in your environment.
Microsoft has produced hundreds of pages of documentation pertaining to securing privileged access. Portions of the documentation for configuring PAWs are still pending an update from Windows 10 to Windows 11. But many of us don’t have time to read all the documentation or build our own PAW deployment strategies. Start your PAW implementation now by contacting the experts at Ravenswood Technology Group for assistance. Reach out today!










