The prevalence of password spray attacks reflect the argument that passwords are often considered poor security. People have been creating weak passwords (usually unintentionally) since the advent of the concept. The difference now is that attackers have caught on not only to the risk of bad passwords, but also more importantly, to the patterns of human behavior that often lead to passwords that are easy to guess. The real solution to preventing password spray attacks is completing the journey to passwordless authentication. For most organizations, though, this is a long and complicated process. Until passwordless authentication is a more viable option, we must take steps to defend against password spray attacks. Entra ID (formerly Azure Active Directory) can help.
What Is Password Spray?
Password spray is a form of brute force attack that is both difficult to detect and frequently very effective. Traditionally, an attacker would try countless combinations of passwords against a single account in the hopes of finding a match. Account lockout policies in Active Directory (AD) are designed to protect against this. These attacks are easy to detect and are frequently thwarted by lockout controls.
Password spray works in a different manner. Instead of trying various combinations on an account-by-account basis, attackers try one possible password against many accounts. When they fail, they wait an extended period and try a new combination. These types of attacks are difficult to detect since they appear in logs as a single failed sign-on. They also rely on behaviors that lead people to select bad passwords.
For example, many organizations have password expiration policies that require end users to choose a new password quarterly, or maybe twice a year. These types of policies often lead to end users choosing passwords based on patterns where they only modify a small component of their password each time it expires, to make the password easier to remember. For example, someone might choose a password of Summer2021! if their password expires at the end of spring. When the password expires again, 90 days later, the same person might choose Fall2021! as their new password. The names of local sports teams and office locations are two other frequent examples. Common passwords found in leaked credential dumps also influence the patterns chosen in a password spray attack. These patterns are common and predictable and are exactly what attackers use when launching a password spray attack, as Figure 1 shows.
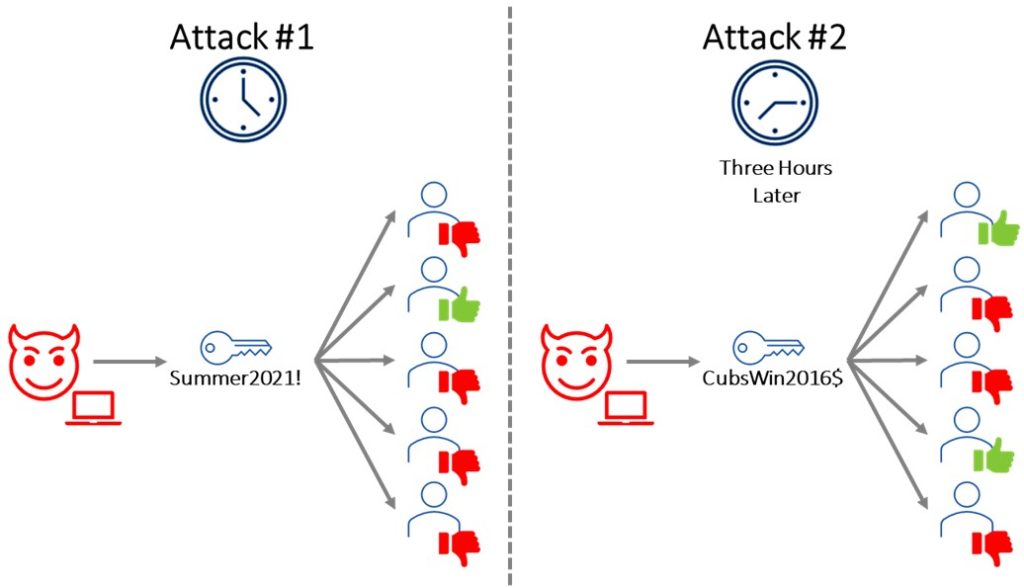
In Figure 1, the attacker tests the password Summer2021! for a set of users and succeeds with one user. About three hours later, the attacker tries the password CubsWin2016$ and succeeds with two additional users. Since these attempts were spread several hours apart, and only resulted in one failed authentication attempt for each user, chances are the organization’s monitoring systems won’t catch it. Meanwhile, the attacker has obtained valid credentials for three users.
How Entra Password Protection Helps Prevent Password Spray
Although password spray is difficult to detect as a single entity, mass scale identity platforms such as Entra ID have much larger data sets that make these patterns detectable. Microsoft does exactly this and curates password spray attack data in multiple forms for Entra ID Premium customers. Through billions upon billions of authentication attempts, Microsoft can curate a list of some of the most common passwords that are used in password spray attacks. The company uses this data to prevent end users from choosing these passwords, as Figure 2 shows, when they change their password in the cloud.
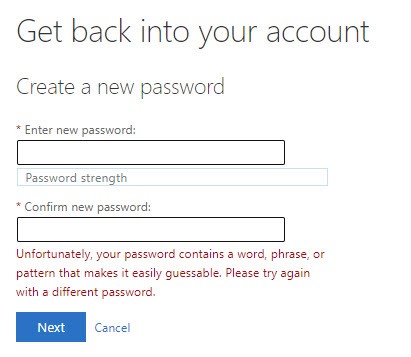
When a user selects a bad password, as determined by Microsoft, Entra’s self-service password reset system reports that “Unfortunately, your password contains a word, phrase, or pattern that makes it easily guessable. Please try again with a different password.”
This feature is great if all your password changes occur in the cloud. But this isn’t the case for most organizations. Instead, a large percentage of password changes happen in on-premises AD. To address this need, Entra ID Premium includes a feature called Entra Password Protection. With Entra Password Protection, you can install a password filter on all your domain controllers. The password filter receives a copy of Microsoft’s database of weak passwords and blocks the use of them during password change operations. You can also provide your own prohibited keywords to include in the database. For example, you might include the name of your organization, the streets that major office buildings are on, etc.
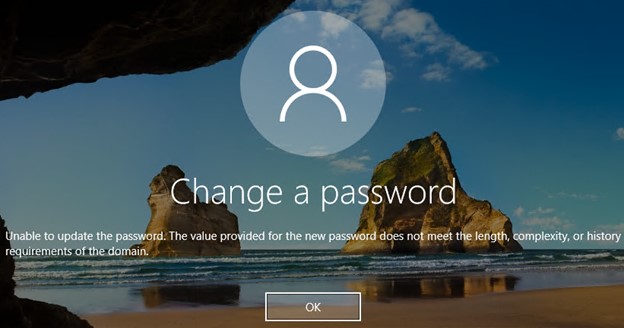
Deploying Entra Password Protection will require updates to documentation and processes, especially with respect to your service desk and end-user support teams. The mechanism that Windows uses to communicate an invalid password when a user changes their password hasn’t changed since Windows NT. As a result, the error that Entra Password Protection generates, shown in Figure 3, is the exact same error as when a user chooses a password that doesn’t meet complexity requirements. This can lead to confusion since the user may have chosen a password that is technically considered complex (such as Summer2021!) but is actually a poor password.
You can initially deploy Entra Password Protection in a passive, audit mode to collect data about what the potential impact is. Each time Entra Password Protection blocks a password change, an event is logged on the domain controller processing the request. You can collect this data using a Security Information and Event Management (SIEM) system for 30-60 days and then aggregate it to identify patterns and expected impact. Once you’ve prepared, you can reconfigure Entra Password Protection to act in enforcement mode. Data will continue to be logged, but bad passwords will also be blocked.
What’s Next?
If your organization is like most, passwordless authentication is a journey that is only the beginning. We highly recommend that anyone with Entra ID Premium and an on-premises AD implementation deploy Entra Password Protection. You can learn more about how we utilize Azure Multi Factor Authentication here. Additionally, we also often recommend revisiting antiquated password policies and updating them to reflect modern guidance and standards. These steps are important defenses against weak passwords and password spray attacks that can lead to a larger compromise event.
Need advice on your Active Directory installation or Windows security setup? Contact the experts at Ravenswood Technology Group for help today.