As organizations embrace cloud technologies and modernize their authentication methods, they must still maintain support for their legacy on-premises environments. A key step in transitioning to a cloud-first strategy is extending on-premises Active Directory (AD) identities to a cloud identity provider. For many, this is accomplished through Microsoft Entra Connect Sync, which synchronizes identities and attributes from AD to Entra ID through sophisticated directory synchronization processes.

While Connect Sync remains fully supported, Microsoft has introduced a new syncing solution, Microsoft Entra Cloud Sync, which is designed to simplify and enhance the synchronization process. Cloud Sync not only performs many of the tasks previously handled by Connect Sync but also offers greater flexibility, additional features, and reduces reliance on on-premises infrastructure. These improvements are prompting many organizations to reconsider their synchronization strategy and evaluate whether it’s time to migrate from Connect Sync to the more modern Cloud Sync agent.
Microsoft Entra ID Connect Sync: The Traditional Solution for Maintaining Hybrid Identities
Partner with Microsoft experts you can trust
If it’s time to take that first step toward leveling up your organization’s security, get in touch with Ravenswood to start the conversation.
Connect Sync has evolved over the years through several iterations (e.g., DirSync and Azure AD Connect Sync V1). The latest release, Microsoft Entra Connect V2, is an updated version of the same software, with the core functionality remaining unchanged: extending on-premises identities to the cloud for authentication to cloud resources. This is achieved by storing data about synchronized objects in the local connect database and processing changes through the Synchronization Engine service, which runs on the Connect Sync server.
Entra Connect V2 introduces several security improvements, such as support for TLS 1.2, migration from the Azure Active Directory authentication library (ADAL) to Microsoft authentication library (MSAL), and an upgrade to SQL Server 2019 for the local database.
Despite these improvements, the complicated on-premises infrastructure and upgrade procedures remain a challenge. These limitations continue to create difficulties for hybrid identity administrators, especially for organizations with complex synchronization topologies that span multiple AD forests and rely on Connect Sync.
For example, Figure 1 illustrates an environment with three forests across two separate networks. The environment uses an active-passive Connect Sync configuration with a separate connect database for each server. To enable Connect Sync, network connectivity has been established between Network 1 and Network 2. A network firewall filters traffic between the networks to minimize exposure to the forests in Network 1. The complexities in these infrastructure requirements, especially the need for network connectivity between disconnected forests have caused additional infrastructure to be implemented, including additional network appliances, dedicated servers for the Connect Database, cloud storage solutions for backup redundancy, and a staging server. The staging server does not participate in synchronization load during normal operations; it is only used during manual failover from the active sync server to the passive staging server as part of a swing migration for updates or outages.
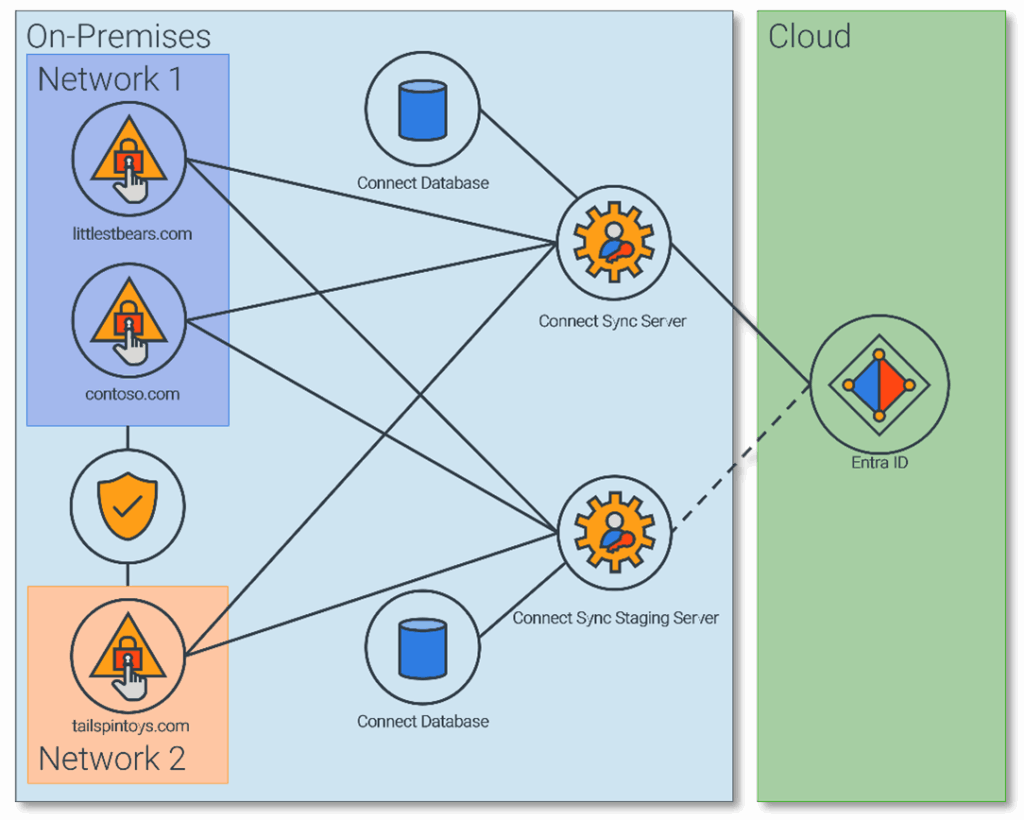
While many organizations continue using Connect Sync to synchronize identities with Entra ID, Microsoft has introduced a new agent to further modernize the synchronization process.
Microsoft Entra ID Cloud Sync: A Cloud Native Solution for Your Synchronization Needs
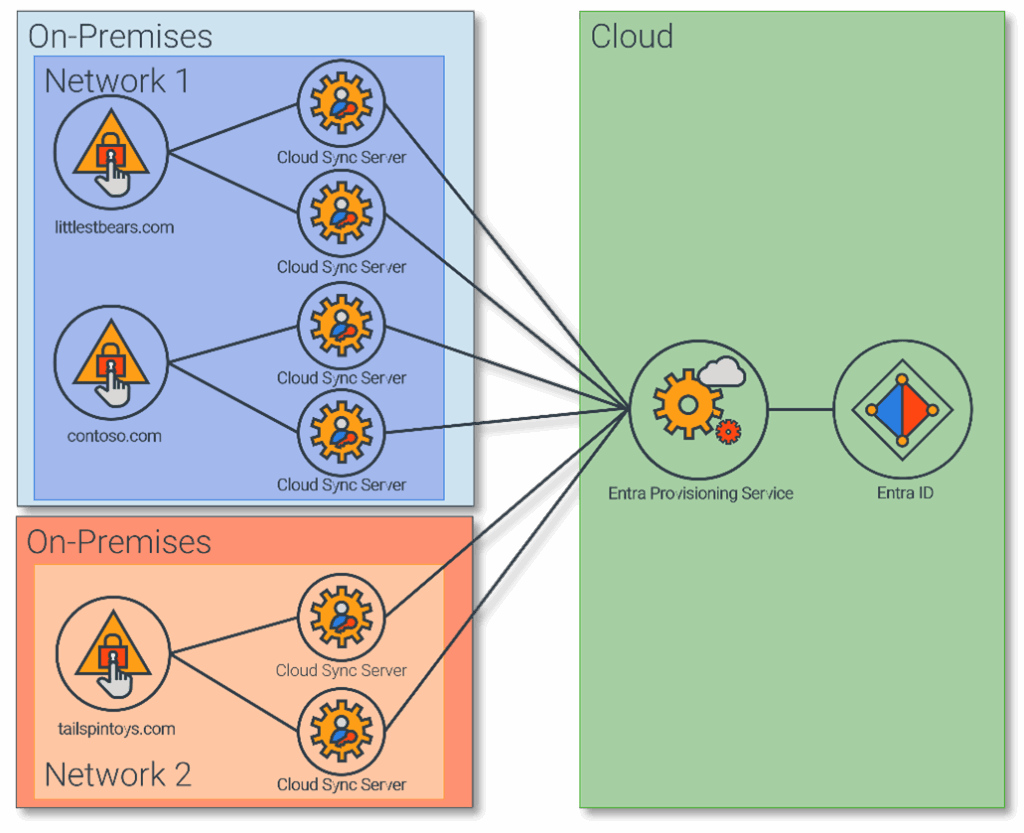
However, Cloud Sync does not currently support the same wide range of synchronization scenarios as Connect Sync and does come with its own complexities.
Preparing for Connect Sync to Cloud Sync Migration
With a well-planned migration, both Connect Sync and Cloud Sync can coexist until the migration is complete, ensuring a smooth transition and minimizing disruption. Assessing your organization’s readiness for Cloud Sync starts with evaluating your current Connect Sync implementation and AD Forest configuration. While Cloud Sync supports many scenarios, there are notable exceptions, including environments which require Hybrid Join devices to manage devices which are connected to their on-premises AD domain, large AD domains with over 150,000 objects and complex synchronization scenarios such as Exchange Server resource forests.
Unsupported Configurations
Although Cloud Sync has seen significant improvements and can now support a variety of configurations, it still lacks the depth of the current Connect Sync client. Connect Sync remains the only client capable of supporting many of the complex configurations required by enterprises.
Hybrid Join Devices
The lack of support for Hybrid Join devices will make Cloud Sync unsuitable for many enterprise customers, as many still rely on on-premises authentication protocols. These organizations often require Hybrid Join to ensure seamless integration between their on-premises Active Directory and Entra ID environments. Without this support, they cannot migrate to Cloud Sync by converting their devices to Entra Join without losing access to critical on-premises resources, which could lead to significant disruptions in their operations and workflow.
Exchange Resource Forests
Enterprises with complex Exchange implementations will need to rethink their plans to migrate to Cloud Sync, as it currently does not support all scenarios, such as Exchange resource forests or dedicated Exchange forests. These configurations involve housing accounts and mailboxes in separate forests and using custom attribute matching to merge accounts in Entra ID. As a result, organizations will need to continue to utilize Connect Sync.
Migration Readiness
Before migration, hybrid identity administrators should assess their environment’s compatibility. Microsoft has streamlined this process by providing the Check Sync Tool, which helps evaluate whether Cloud Sync is a suitable option. This tool allows administrators to assess their current synchronization configuration and determine if it aligns with their organization’s needs. While some configurations may immediately disqualify Cloud Sync, others may require adjustments to the existing setup for compatibility.
Authentication
Cloud Sync currently supports Password Hash Sync (PHS) and federation, but it does not support Pass Through Authentication (PTA). If your organization is still using PTA, it may be worth assessing PHS as an alternative. Depending on the specific requirements that led your organization to use PTA, you may find that transitioning to PHS is straightforward and provides additional benefits.
Transitioning to PHS provides the opportunity to enable additional Entra ID services, such as allowing your organization to leverage Microsoft Entra ID Protection, which can detect if any users’ credentials have been compromised, helping mitigate potential risks to your organization. When combined with user risk detections and risk policies, users who fall victim to credential harvesting attacks can be prompted to reset their passwords before completing authentication to cloud services.
Device Writeback
If you’re using device writeback solely for Windows Hello for Business, Microsoft continues to support this important passwordless sign-in experience with the Windows Hello for Business Hybrid Cloud Kerberos Trust deployment model, detailed in the Windows Hello for Business Cloud Kerberos Trust Deployment Guide. Although this requires additional configuration before migrating, it offers the benefit of eliminating the need to maintain complex public key infrastructure (PKI) and waiting for Connect Sync synchronization.
Upgrade Connect Sync
It is required that organizations ensure they are using the latest version of Connect Sync to ensure that Cloud Sync migration goes smoothly. Depending on the environment’s architecture, this may involve simply upgrading the primary server. However, in most cases, a swing migration will be preferred for more advanced deployments, which include primary and staging servers. The steps for this migration can be found in the Microsoft document: Microsoft Entra Connect: Upgrade from a previous version – Swing migration.
Approach to Migration
A successful migration starts with thorough planning. This includes identifying the objects currently being synchronized and testing similar objects in a controlled test environment. The non-production and production migration should both follow a similar approach to ensure that the process has been thoroughly tested. These migration milestones have been outlined in Table 1: Pilot Migration, Migration Execution, and Migration Completion.
Pilot Migration | Migration Execution | Migration Completion |
|---|---|---|
Table 1 – Migration Approach | ||
|
|
|
Pilot migration begins with identifying low-risk candidates from each of the supported categories: users, groups, and contacts. These candidates are filtered from the object attribute synchronization flow using custom Connect Sync inbound and outbound rules, and they are scoped into Cloud Sync using scoping filters.
This strategy allows Connect Sync and Cloud Sync to coexist during the transition, enabling a smooth handoff between the two synchronization agents. The steps involved in this process are outlined in the Pilot Migration column of Table 1. Note that the pilot migration may involve multiple phases, with each phase repeating the same steps.
After a successful pilot migration, the remaining in-scope objects should be divided into migration phases. Between each phase, verify that the objects have been successfully filtered from Connect Sync and are being provisioned correctly by Cloud Sync. These validation steps ensure that each migration wave works as expected before moving on to the next. Much of the migration will take place during these phases, which are detailed in the Migration Execution column of Table 1.
Once all eligible objects have been filtered from Connect Sync, the synchronization scheduler should be stopped. This action disables provisioning from the on-premises Connect Sync agent while still allowing for quick reactivation if any issues occur. After a suitable observation period, you can proceed with fully decommissioning the Connect Sync agent and all related infrastructure. These final steps, which include uninstalling the Connect Sync agent, are described in the Migration Completion column of Table 1.
Conclusion
While Connect Sync is still fully supported and has no announced end-of-life date, it may be time to evaluate whether your organization should start planning for a migration from Connect Sync to Cloud Sync, or if Connect Sync can serve as a valuable tool in your cloud-first strategy. When weighing AD Connect vs Cloud Sync options, organizations must carefully consider their specific requirements and infrastructure constraints.
Even if you’re not ready to start the migration now, it’s a good idea to begin reviewing your current synchronization configuration and consider the following questions:
- What form of authentication is my organization using for Entra ID?
- Is my primary Connect Sync server running the latest version?
- Has my staging Connect Sync server been upgraded to the most recent version?
- Have I recently tested my staging server to ensure it can function if the primary server fails?
If you need guidance on determining whether your organization is ready to migrate to Cloud Sync or assistance in evaluating your current Connect Sync configuration, don’t hesitate to reach out to Ravenswood today.











