Identity and Access Management (IAM) solutions are critical in today’s world for businesses of most sizes—not just from a user experience and productivity perspective, but also from a security standpoint. Without an IAM solution, organizations don’t have a reliable identity life cycle management process.
When an identity from Active Directory (AD) is synchronized with a cloud-based identity platform such as Entra ID (formerly Azure Active Directory), those identities are classified as being hybrid because changing a user in AD results in a change for that user’s cloud identity. When user accounts are terminated in an inconsistent manner, certain aspects of the termination process may fall through the cracks, which can result in security risks for an organization.
The goal of this article is to outline some essential practices for automating the life cycle and termination of hybrid users.
1. Monitor Licensing Through Identity Management Solutions
All medium and large organizations should have an IAM solution for managing the entire life cycle of identities. For example, when a person is onboarded in an HR system, a corresponding user account should be created in AD. When the person’s manager changes in the HR system, that change should reflect in AD. When the person is terminated, relevant changes should again reflect in AD. An IAM solution helps keep these HR system changes implemented in AD in a timely fashion.
When a person is terminated, you need to ensure that the user account gets disabled in AD promptly. For some organizations, this is a regulatory compliance requirement. The hybrid synchronization system will automatically reflect this change in Entra ID for hybrid users.
A dynamic group or groups should be defined with a filter containing only enabled users. The rule should look something like Figure 1, with the minimum syntax defined as (user.accountEnabled -eq true)—and possibly with more rules in the syntax using the AND condition if there are different profiles that have distinct licensing needs for users across the organization.
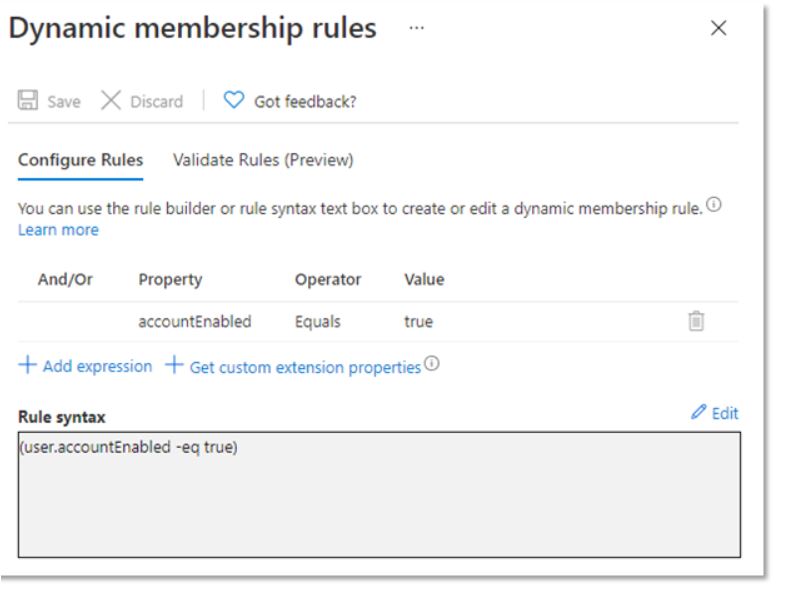
The dynamic group(s) should have Microsoft 365 licenses assigned as part of the automated provisioning process when a user is onboarded. Once a user becomes disabled, that user will fall out of the scope of the dynamic group filter and therefore lose their dynamically assigned licenses.
To properly maintain your directory, there should be a separate process to delete terminated users from AD after the user has been terminated for a set amount of time. Deleting a user in AD will trigger the user’s deletion in Entra ID as well.
2. Delegate Access in Microsoft 365 to Cloud Data and Intune MAM
When a terminated user is no longer licensed for certain workloads in Microsoft 365, there are built-in automated processes for dealing with their Microsoft 365 cloud data. The user’s OneDrive data immediately becomes accessible to the user’s manager for 30 days, which is a configurable duration. The manager receives an email with this information and a link to the data. The manager should copy any required data to another location for safekeeping, such as their own OneDrive account. After the duration expires, the original OneDrive data is deleted automatically unless the data falls under a retention policy. Only a SharePoint administrator can restore the data beyond this point—but only for up to 93 days after the content was deleted, after which the data is completely unrecoverable. This 93-day duration isn’t configurable.
If any Intune Mobile Application Management (MAM) policies were assigned to the user and the user no longer has the Intune license, an automatic app-selective wipe of organizational data occurs on the user’s registered mobile devices.
What happens to the deleted user’s mailbox depends on the applied licenses and policies that have (or haven’t) been implemented. If there are no retention policies applied, the mailbox becomes soft-deleted for 30 days. After the 30-day duration, the mailbox cannot be recovered. Managers will sometimes ask for access to a terminated user’s mailbox, and they likely will need access to the data for more than 30 days. In this scenario, where there is no retention policy applied, it is prudent for a manager and the help desk to be timely in their requests and fulfillment.
3. Implement an Automated Retention Policy
Organizations should have an automated retention policy. The retention policy should be established and documented by the legal department to ensure the automated retention policy matches what is listed in the organization’s documented policy. Any mailboxes that have a retention policy assigned to them where the retention policy is configured to only delete data won’t become inactive when the associated Entra ID user is deleted.
If the retention policy is configured to retain any amount of data or to retain and delete data, and the user is no longer licensed for an Exchange mailbox, the mailbox will automatically have its status set to inactive. When a mailbox becomes inactive, that mailbox cannot be logged into interactively and all email addresses that were associated with the mailbox are removed. This means the mailbox can no longer send and receive email. If a delegate such as the user’s manager requires access to the mailbox, the inactive mailbox can be recovered and converted back to a normal state.
An inactive mailbox’s contents still fall under the retention policy and can still be searched by eDiscovery. As time progresses, if the retention policy states to delete email items older than 180 days, for example, the contents within the inactive mailbox will never be older than 180 days—just like any normal active mailbox under the same retention policy. Don’t mark mailboxes with a litigation hold unless they really are under litigation.
4. Track the Life Cycle of Contract Users
Don’t forget contractor identities. It’s common for organizations to manage the life cycles of contractors separately from employees, which often results in contractor accounts maintaining access to systems even after their contract has finished. This is, of course, a security concern and a license cost concern. Even if the designated contractor doesn’t realize they still have access, a bad actor could end up taking control of the contractor account and then start using it—and likely would be undetected.
Automated Solutions are Essential for Termination of Hybrid Users
To prevent spiraling licensing costs, mitigate some potential attacks from bad actors, and to maintain compliance with the legal department, make it best practice to have an automated solution for terminating users. The automated solution should consider all aspects of the user’s Microsoft 365 identity, such as mailbox data and OneDrive for Business data. Microsoft has already thought of the most common termination tasks an administrator would otherwise need to perform manually. Microsoft’s efforts remove a lot of the guesswork, but some controls, such as a retention policy, must still be implemented by the customer. It’s up to the implementer to test their termination workflow to ensure that everything works as expected. Need help automating the termination of hybrid identities? The experts at Ravenswood Technology can help. Contact us today.










