User attributes are important metadata that should be treated with care. Some organizations do not take user attributes seriously enough, which creates problems when the company tries to automate system access.
When Active Directory (AD) users are synchronized with a cloud-based identity platform such as Entra ID (formerly Azure Active Directory), those user identities are then classified as being hybrid because changing an on-premises user object in AD results in a change to that user’s cloud identity. Having inconsistent attribute values synchronized to Entra ID only compounds the problem.
To effectively manage user attributes in your organization, you must first understand the best practices for handling user principal names (UPNs), email addresses, and other attributes.
1. Managing the User Principal Name
Make sure to verify your organization’s domain names in Entra ID and add the UPN domain suffixes to the AD domains that are or will be synced. Every user’s UPN should match their Mail attribute in AD. The Mail attribute represents the primary SMTP address of the user’s mailbox and therefore is a single-value attribute, which makes it possible to easily keep the UPN value the same as the Mail value. For the best user experience, UPNs should be consistent between AD and Entra ID. If you are already using a non-routable UPN (e.g., john.smith@abc.local) for your users in some on-premises applications, have a discussion with those application owners to coordinate and update the UPNs in AD and the related applications to match their Mail attribute where appropriate.
2. Assigning Predictable Email Addresses
Configure an email address policy that automatically sets the user’s primary SMTP attribute based on company policy. If there is no company policy for users’ primary SMTP addresses, discuss and establish a policy. Remember that users can have alternative SMTP addresses that diverge from the company email policy. Email messages sent to a non-primary SMTP address will still be delivered to the user’s mailbox. However, company branding should take precedence in determining the primary SMTP address.
3. Managing User Attributes
If your organization has an automated process or system such as an identity and access management (IAM) solution that synchronizes identities from an HR system to AD, the solution should automatically update a user’s UPN when their Mail attribute changes. This is typically important for users who go through large life changes that involve a legal name change (e.g., marriage, divorce), since many organizations use the user’s last name as a part of their email address. The IAM solution should also assign a manager on the subordinate user in AD on a persistent basis, which is important for workflow automation processes and life-cycle processes for some Microsoft 365 services. The only person with a hybrid identity that may not have a manager assigned to them is the CEO.
Many other attributes are also important for hybrid identities. Attributes that should be populated in a consistent manner include but may not be limited to Department, Title, Company, and Office. To maintain consistency, don’t use variations of terms. For example, for the IT department, don’t use values such as I.T., IT, and Information Technology to represent the same department. Pick a term and stick with it—or better yet, have an automated process or system to simply synchronize the values from the HR system to AD. If HR’s data is inconsistent, you’ll need to have a discussion to correct that problem. When attributes are populated in a consistent manner, you can create dynamic Entra groups that can then be used for assigning access to things such as enterprise applications. For example, all users who have a department value of Sales belong to a group called Sales Users, which can be used to grant access to an application like Salesforce.
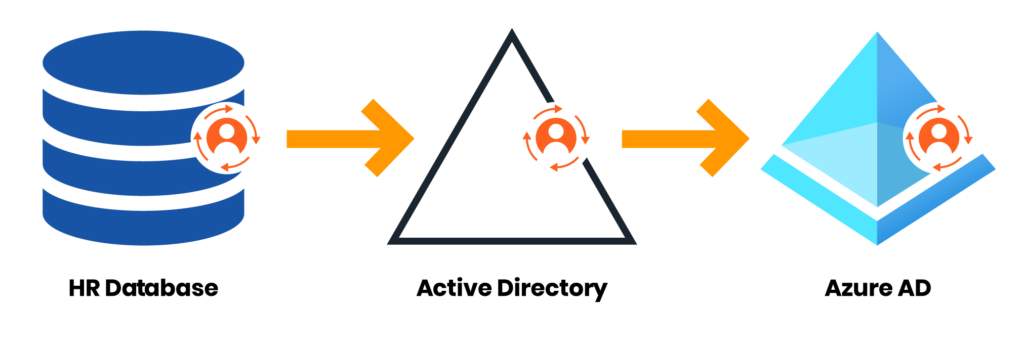
4. Consistency Is Key
Consistently managing data in AD is critical not only for security and compliance reasons but also to ensure that applications and Office 365 workloads work as expected. Implementing automation is crucial in all but the smallest organizations. Without automation, data in AD will inevitably diverge from the source of truth over time.
Need help managing your Active Directory data? The experts at Ravenswood Technology can help. Contact us today.










