One of the most important security controls in an Active Directory (AD) forest is the prevention of privilege escalation paths. When privilege escalation is possible, an adversary may move laterally through the network (e.g., from client computer to client computer or member server to member server) until they find an opportunity to capture credentials that provide a mechanism to elevate privileges, eventually reaching domain admin access. The tiered access model for AD introduces a significant number of technical controls that reduce the risk of privilege escalation.
The Tiered Access Model
The tiered access model is composed of three tiers, as Figure 1 shows:
- Tier 0 – Assets that provide direct control of security and identity infrastructure. AD is the preeminent Tier 0 asset, but other common examples are services such as public key infrastructure (PKI), Entra ID Connect, Entra ID, identity and access management (IAM) tools, federation (e.g., AD FS, Ping, Okta, etc.), and management systems for Tier 0 assets.
- Tier 1 – Servers, applications, and cloud services. Tier 1 access typically provides a significant amount of access to critical business data. Within Tier 1, it is not uncommon to further segment access to limit privileged access to different sets of servers, applications, and services.
- Tier 2 – Client computers and related devices. Administrative access or indirect control (e.g., help desk/desktop support) of an end-user device is the most common example of Tier 2 access. Within Tier 2, it is permissible to further segment access to limit privileged access to different sets of Tier 2 assets.
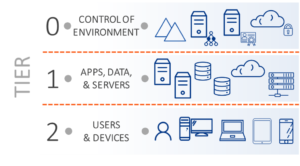
Figure 1 Tiers in the tiered access model
Figure 2 shows another way to look at the tiered access model. Actors in each tier are permitted to control their tier; when necessary, they can also control a lower tier. However, a lower-tier actor is never allowed to exert control on a higher tier.
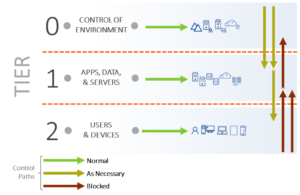
Figure 2 Permitted control paths
Tiered Access Model Implementation
The critical part of the tiered model is the implementation of technical controls that prevent privileged credentials from intentionally or accidentally crossing tier boundaries, as Figure 3 shows. When credentials cross tier boundaries, they become susceptible to compromise through credential theft and other avenues. Technical controls are implemented with Group Policy Objects (GPOs) to prevent these situations.
GPOs must be created to prevent each of the blocked logon paths shown in Figure 3. Typically, these GPOs configure security rights that both permit and deny access, including:
- Allow logon through Terminal Services
- Deny access to this computer from the network
- Deny logon as a batch job
- Deny logon as a service
- Deny logon locally
- Deny logon through Terminal Services
For example, in Tier 1, Tier 0 groups such as Domain Admins will be denied access and in Tier 2, Tier 0 groups and Tier 1 groups (such as member server administrators) will be denied access. Built-in groups that should not be used in a best practices AD environment such as Account Operators or Backup Operators are also denied access.
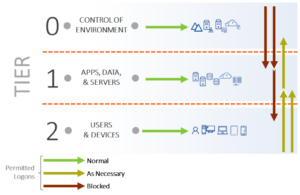
Figure 3 Permitted logons
Planning an Implementation
Implementing the tiered access model in your AD environment is not an overnight process. There is often a significant amount of work to identify where applications and IT processes will break or otherwise be impacted by the tiered access model. Because of this, it is usually more effective to structure an implementation in phases. Begin with where you can obtain the most value: protecting Tier 0. The ultimate goal of any adversary is to obtain complete control, and in an AD forest, complete control is possession of a domain admin credential.
Once you have completed Tier 0 you can begin exploring the effort required to protect Tier 1 credentials. This phase is often much more labor intensive. You may need to further segment Tier 1 based on risk and then apply protections to credentials used to manage the highest-risk member servers. These could be servers with business-critical applications or servers that house sensitive data such as financials or intellectual property, for example.
Tiered Access Model Expertise
Securing privileged access to AD is something the team at Ravenswood does every day. Whether you’re considering implementing the tiered access model or have decided to embark on this path, our team can help assess the risk in your AD environment, plan a strategy to address your needs, and implement the tiered access model as well as other critical AD security controls. Contact us to discuss how we can help.













